TryHackMe: Pickle Rick
Goal: Find three files that contain ingredients for Ricks potion so he can transform himself back into a human from a pickle
Eastern Washington University BSCS: Cybersecurity 101 extra credit
I began by firing up nmap scanner to discover open ports on the victim’s machine. I included OS Detection, Service Detection, and Default Scripts.
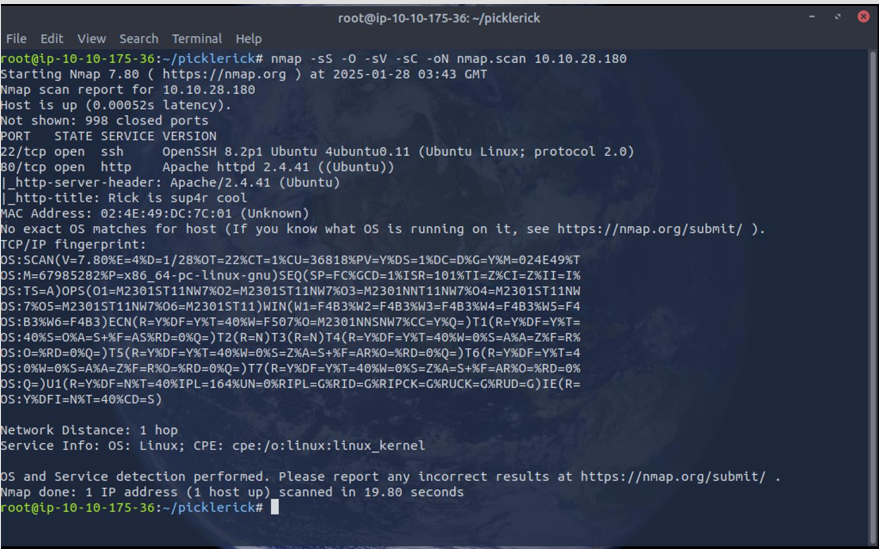
Looks like the victim machine is running Ubuntu with two open ports with port 80 running Apache and SSH on port 22 running OpenSSH. Next, I wanted to find out what is running on the web server on port 80.
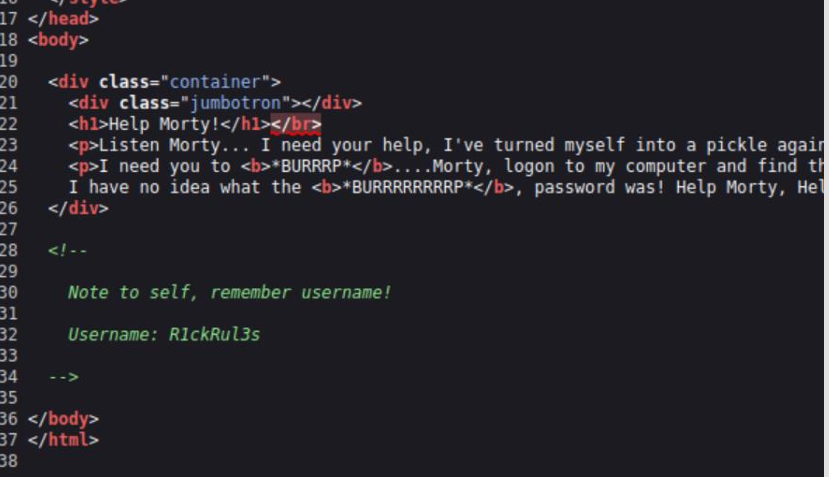
At first glance, nothing of interest can be seen. I decided to look at the source code and discovered a comment “Username: R1ckRul3s”, which appears to be username Since I have done CTF’s before I always have a habit of checking if the server has robots.txt file which, in some cases, can contain juicy information. In this case, robots.txt only contained one word “Wubbalubbadubdub”. My first guess that this may be username password combination. So I tried logging in with R1ckRul3s:Wubbalubbadubdub via SSH on port 22 without success. Moving on.
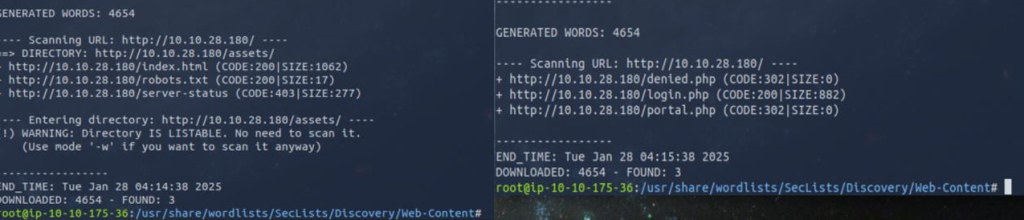
Next, I fired up dirb a tool that brute-forces a web server by trying out lists of common file and directory names (wordlists). This helps me discover hidden files, directories, and scripts that are not normally linked on the site but still exist on the web server (e.g. /backup). The results of dirb are as good as your wordlist and your use of the tool. I ran dirb against the server using a default wordlist named common.txt. First run (Figure 4), I searched for directories only and the second run (Figure 5), I searched for files with a *.php extension. The only directory I found is assets that contains three .php files login.php, portal.php, and denied.php.
The asset folder only contained some photos that were no interest to me. But I did discover a login form /login.php.
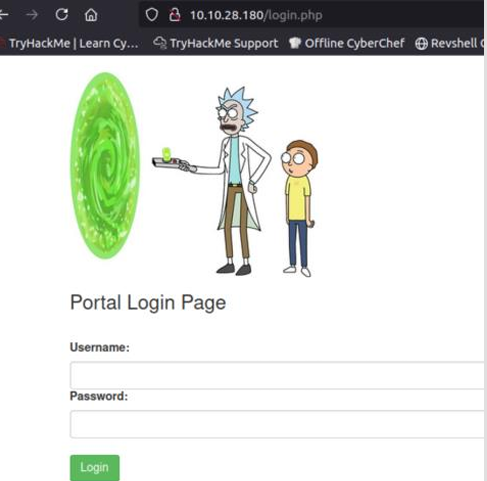
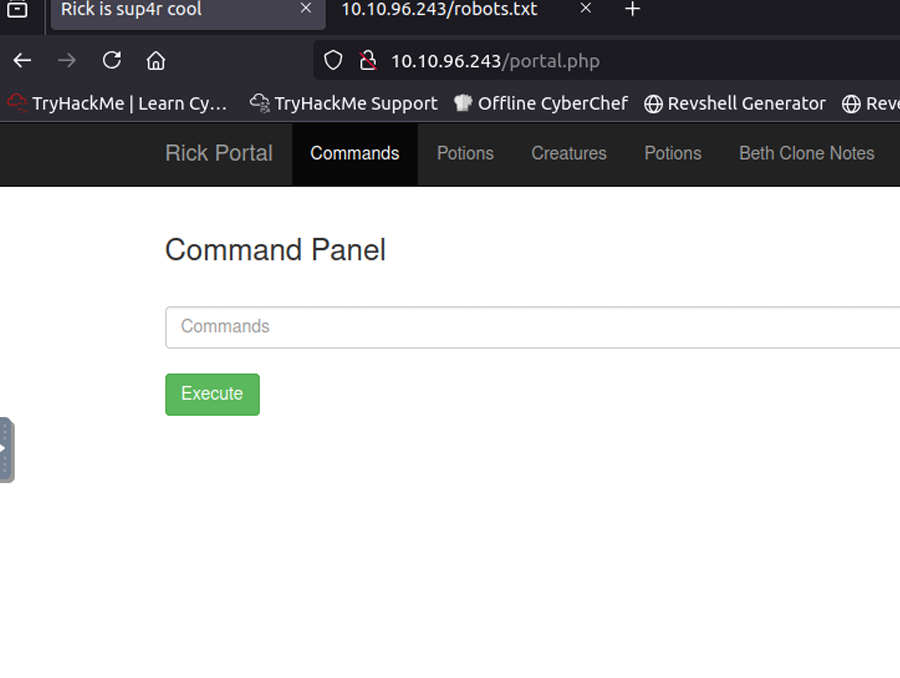
My first instinct was to try the username and password that I found R1ckRul3s:Wubbalubbadubdub in the source code of the main page and in /robots.txt. Success! I am prompted with an input box that is labeled Command Panel. Having command execution through the web server is the next best thing to getting a reverse shell. Other links “Potions” “Creatures” and “Beth Clone Notes” just took me the same page showing a photo of Pickle Rick. Source code of the links showed nothing promising just that all the hyperlinks were linked to the same page /denied.php.
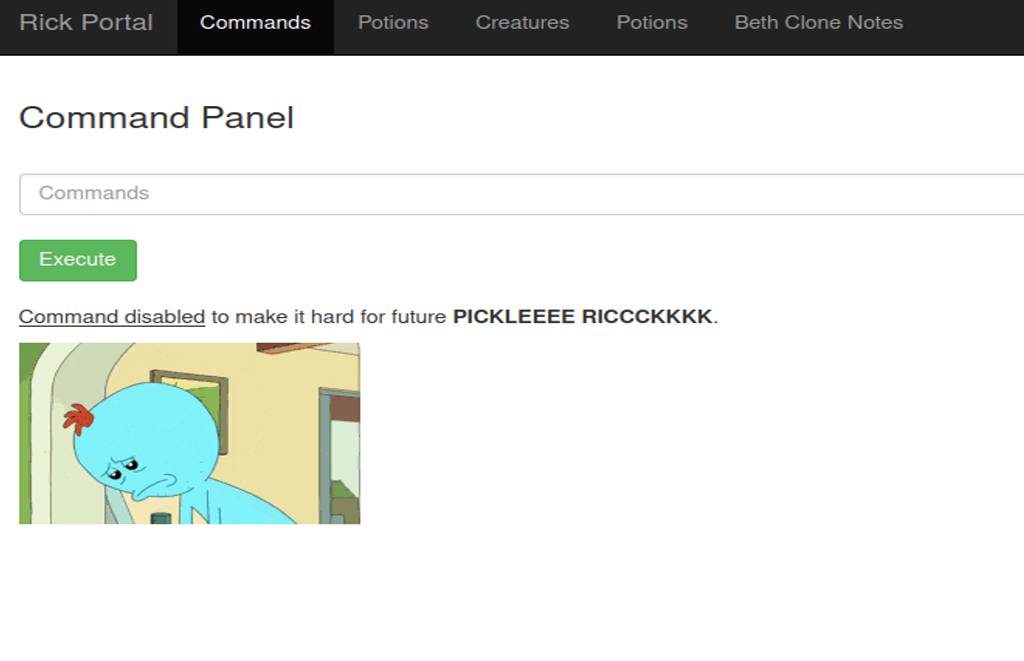
Looks like I can execute commands on the server. Commands are being run as the web server with user “www-data” according to whoami command. I wanted to see what users exist on the machine, “cat /etc/passwd” got me output of “command disabled”. Figure 8 shows the output of trying to cat /etc/passwd. Appears that some commands are disabled to make it hard for future Pickle Rick. Don’t worry Pickle Rick, we will go on and find your three recipes!
I tried several ways to see if I can bypass disabled command of “cat”, “less”, “more” and others. Trying “id; cat /etc/passwd” along with some other techniques didn’t help. I'm guessing "cat" is simply blacklisted. I tried obfuscation techniques such as base64 encoding and using Unicode escaping without luck. If cat doesn’t work, no problem because there is always alternatives such as bat, mdcat, grcat, tac, ccat, see, lolcat, less, head, tail, more, nl and many more. I went through a couple and “tac /etc/passwd” worked as well as “nl /etc passwd”. I didn’t try any others because I just need one to work so I am able to read files. Using “nl /etc/passwd” I got the following output (Figure 9).
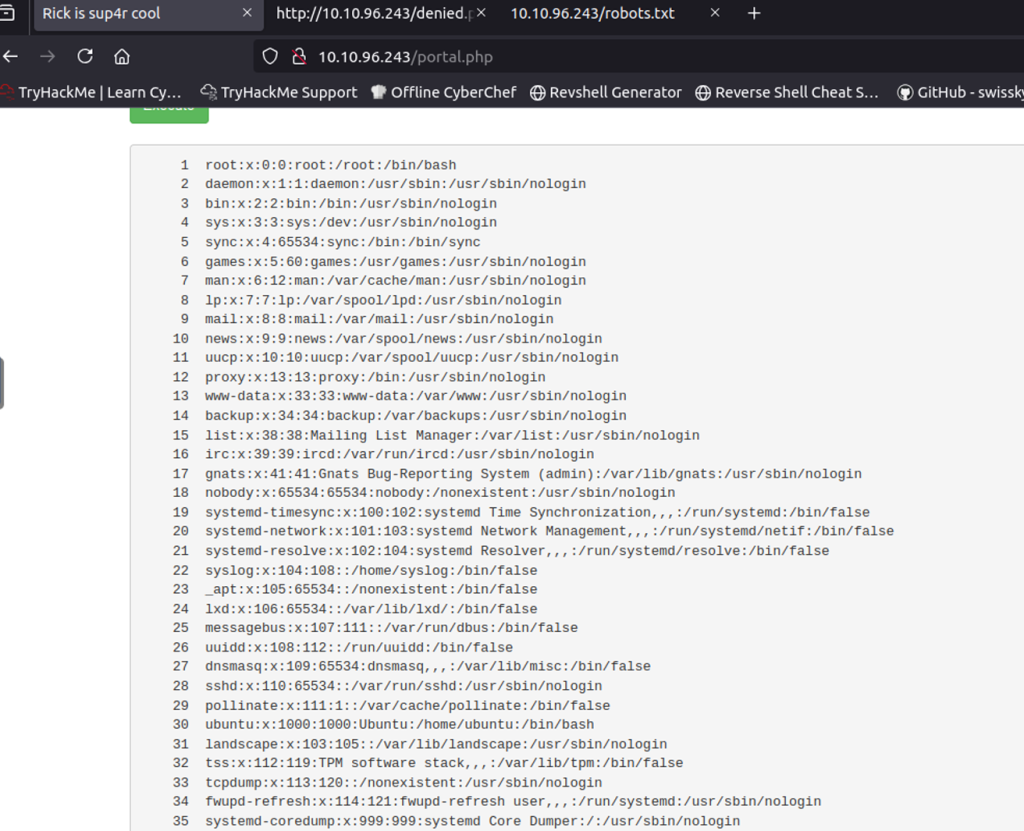
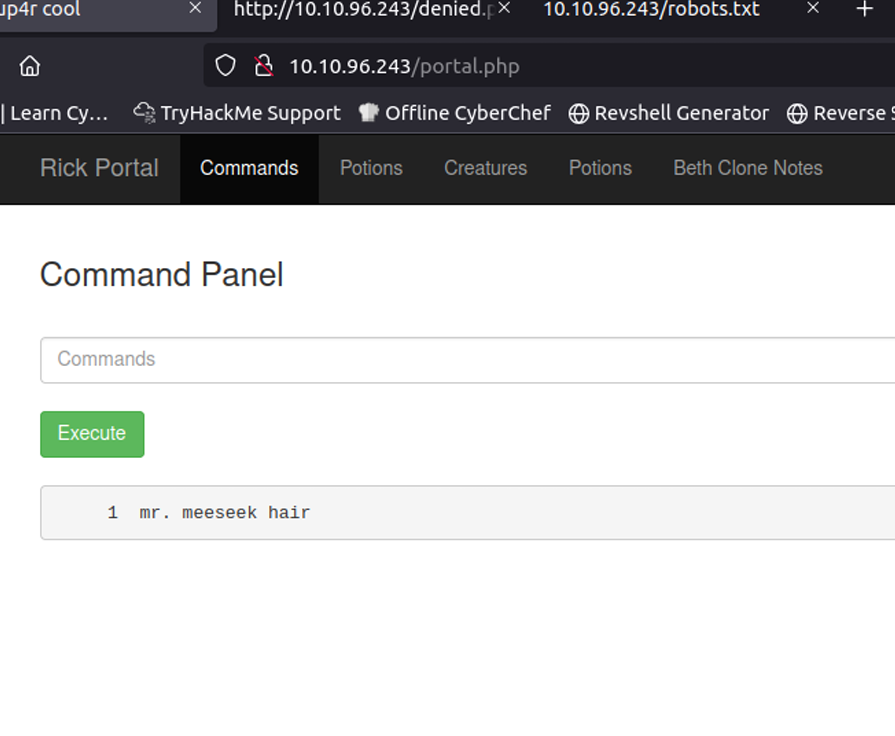
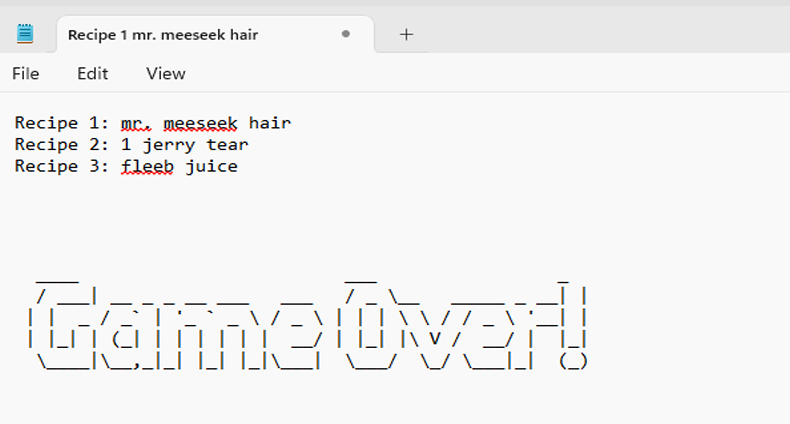
Looks like there are only three users who are able to login root, ubuntu, and rick. Next I wanted to see what /home/ubuntu contained. Nothing of value it was empty. Next, I wanted to view my current directory which was pointed to /var/www/html which I know is the default directory for web servers. Looking inside /var/www/html, lucky for Pickle Rick, I discovered his first recipe to become a human. Life must be tough being a pickle where everyone just wants to eat you. The first recipe file is named “Sup3rS3cretPickl3Ingred.txt”. Reading the first recipe “Sup3rS3cretPickl3Ingred.txt” in /var/www/html gave me the first recipe of “mr. meeseek hair”. Looks like Rick seeks hair for his first recipe.
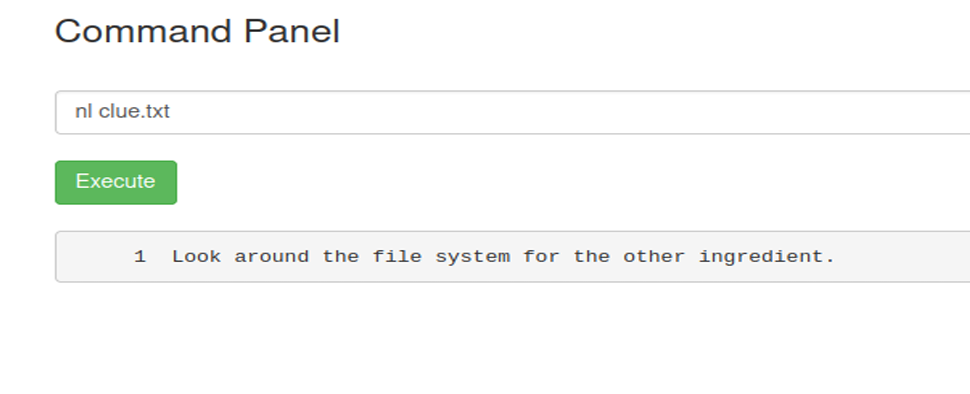
I found a file called clue.txt in the same directory /var/www/html
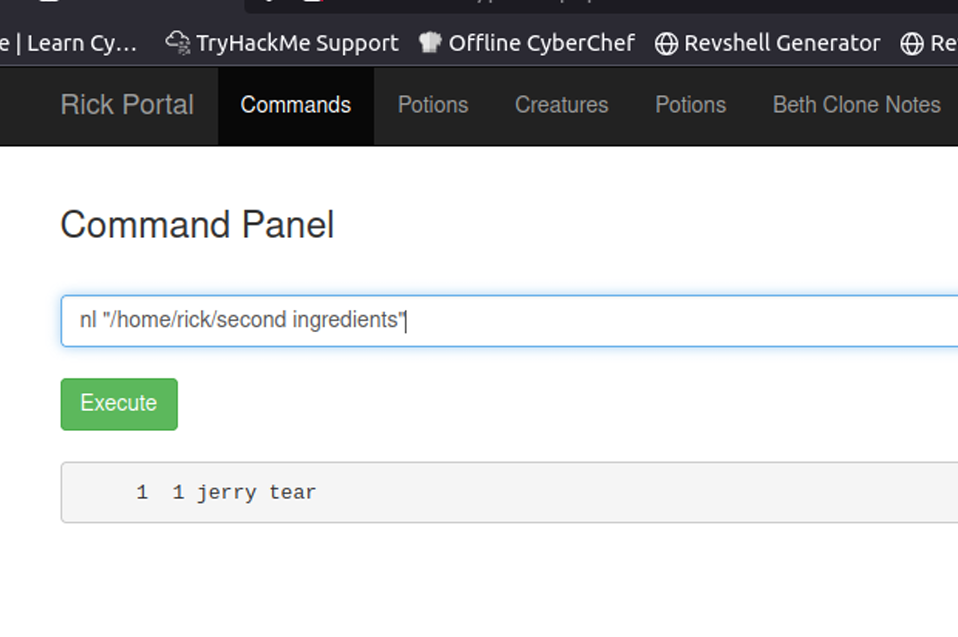
Since the first user ubuntu didn’t have any files I checked /home/rick to see if I can find anything. That’s where I found Rick’s second ingredient which is appropriately named “second ingredient” in ricks home directory. Since there is a space in second ingredient file, I used the command with the directory being in double quotation marks nl “/home/rick/second ingredient”. Our second ingredient is “1 jerry tear” which I cannot begin to guess what that means.
Looking for the last ingredient I thought I would take advise from clue.txt which said to look throughout the file system. Since I don’t know the exact name of the third ingredient considering the first and second ingredients had completely different file names I still decided to use the find command and take a chance. I tried different variations searching “find / -type f name “ingred” and other combinations without luck. Then I forgot that I never checked /root folder or its permissions. Not surprisingly, I wasn’t able to view the contents. Trying ssh with ubuntu and rick as the user and “Wubbalubbadubdub” as the password was not successful. The SSH output was
Permission Denied (publickey) which is possible that SSH is configured in a way that only logging in with private keys are accepted and not passwords.
After searching around I realized I never checked sudo privileges most likely because www-data should never have sudo privileges or run any commands as sudo but it was worth a check. I was stunned, that I am able to run any command as sudo but most importantly I am able to run any command as sudo without a password since www-data is a service account and does not have a password. Figure 13 shows the output of “sudo -l”.
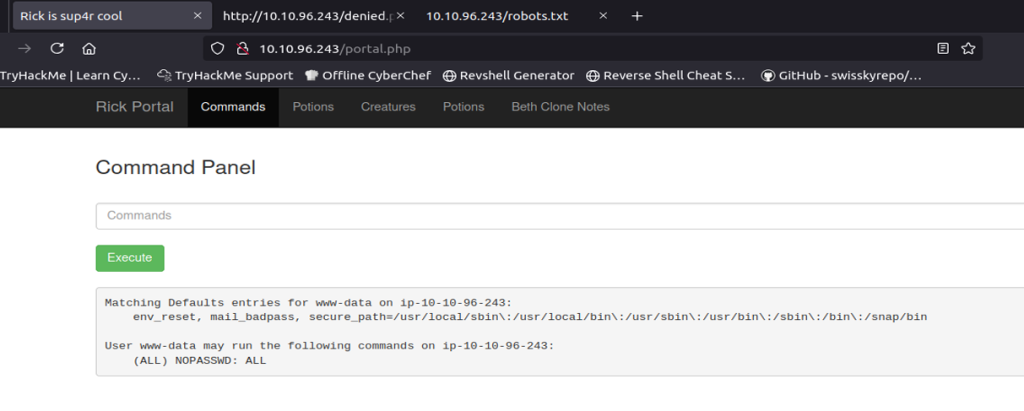
Wasting no time, I used “sudo ls -la /root” to see if the last recipe is in root’s directory.
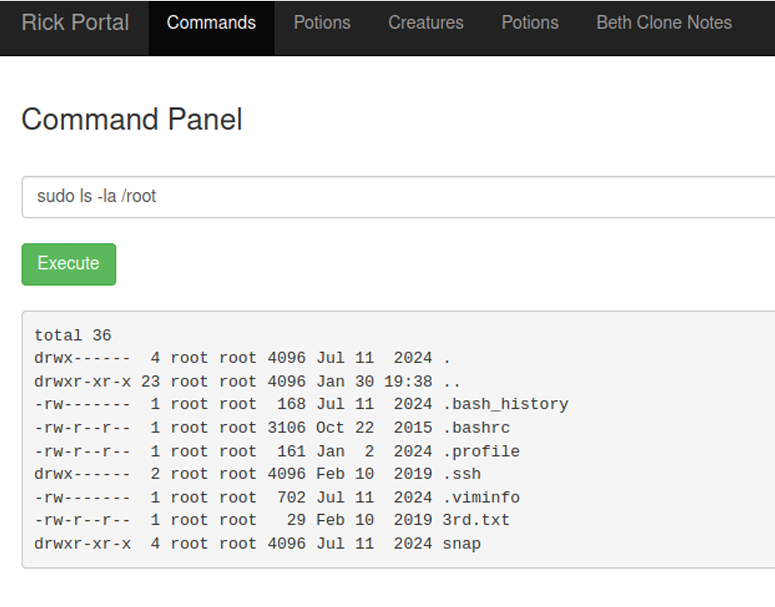
Looks like I did find Rick’s last recipe in a file called 3rd.txt and it is “fleeb juice”. Figure 15 shows the output of the third recipe.
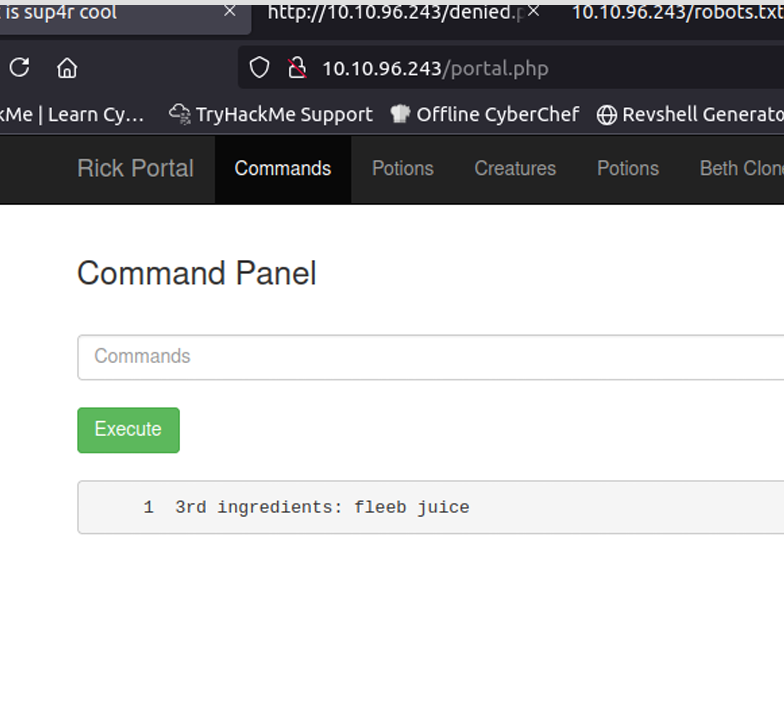
All three recipes have been discovered and it is game over. The three recipes are “mr. meeseek hair”, “1 jerry tear”, and “fleeb juice”. Now Pickle Rick can become a real human, after all, he must be tired being a pickle. I know I would be.
My write-up for TryHackMe Pickle Rick was extra-credit for my Cybersecurity 101 class. Thank you for reading.
I have not failed.
I’ve just found 10,000 ways
that won’t work.Thomas. A. Edison
Leave a Reply